
IT Security
Information security is an essential component for the successful step into digitization. Sensitive company data can only be adequately secured by establishing multi-level technical and organizational security measures and processes.
Causes of digital blackmail, industrial espionage, data leakage and manipulation are often weak points in IT infrastructures and in employee awareness.
This is exactly where we start – with the analysis of weak points and the implementation of specific security measures on the basis of standardized concepts and solutions through ISMS according to DIN IEC / ISO 27001, BSI IT-Grundschutz and VdS 10000.

Oliver Falkenthal
IT Security
Our focus in the area of IT Security are:
Analysis

Security Concepts
On the basis of an actual analysis of IT Security in your company, we create security concepts and develop possible solutions for the greatest possible protection of your IT Landscape. We also support you with the introduction of an ISMS based on ISO 27001 or the VdS 10,000 by means of Protection needs analysis, the Aufst creation of contingency plans and the holistic Realization of a BCM (Business Continuity Management) .
Pentesting
You can only find out whether your company is effectively protected against attacks by hackers if you are waiting for a nasty hacker attack or if you commission us to break into your network with our “good” hackers. With a penetration test, which we adapt to your individual requirements, our certified hackers can test whether a break-in is possible with you with a certain amount of effort or not. We perform pentests externally on websites and company firewalls, but also internally in your company’s network. Finally, you will receive a deficiency report and recommended measures to remedy the problem.
Weak Point Analysis
The attack points of hackers have shifted from the mostly well-secured external firewall to internal attacks. Inadequately secured systems can be tracked down and attacked through internal attacks (e.g. with the help of malware). We therefore recommend performing a weak point analysis on a regular basis, during which all systems are tested for weak points. The resulting report then contains the measures for eliminating the vulnerabilities. The maximum level of security can only be achieved through regular (eg monthly) weak point analysis and removal of weak points.
Forensic Science
Our technicians also carry out forensic analyzes after an incident (e.g. hacker attack, ransomware, etc.) on you. The preservation of evidence has the highest priority. Therefore, the status is saved unchanged before any analysis. Analyzes can then be carried out on the live system (live response analysis) or on copies of the backups by the forensic scientist (post-mortem analysis).
Awareness

Phishing
In a phishing campaign, we send very realistic but fake emails to employees of your company in several stages and then evaluate the reactions to the emails. The final report can be used to initiate further measures such as training or information campaigns in the company. Phishing campaigns usually do a lot more to employees than you might think. There are discussions, fears discussed, reporting channels clarified and ultimately processes for dealing with these emails developed. With little effort, an effective awareness-raising measure is created that reaches all employees.
Training
Despite technically sophisticated measures, the greatest weakness in IT Security is the human component. Therefore, awareness training has become an indispensable part of day-to-day business. Employees learn to recognize the attacks and to react accordingly in order to keep damage away from the company. Contents are, for example, secure passwords, encrypted emails and screen locks, as well as dealing with phishing emails and the risk of social engineering.
Social Engineering
The disclosure of more or less sensitive information in social networks, the willingness to provide information on the phone or by email and discussions about sensitive topics in public represent an important vector of attack for criminals. The information obtained is used to initiate financial transactions, for example. We offer social engineering campaigns that test how your employees react to such attacks. We test how far we can penetrate your company by phone, email or in person. The results are evaluated and measures for improvement are developed with them.
Activities
Hardening (SHP, DHP)
Server systems offer extensive services, components and communication protocols. However, many of them are not maintained or investigated for safety because they are not in use. To avoid misuse, services and old protocols that are not required should be deactivated. In addition, the security configuration of all services should be raised to a high level. This all happens at the push of a button when hardening Windows servers with our Server Hardening Package (SHP). We also offer a solution for hardening databases (MSSQL and Oracle).
Patch Management
In order to achieve a high level of security for systems and applications, regular, automated patch management is essential for all mobile and stationary systems. The focus is on the procurement, testing and distribution of updates for applications, drivers and operating systems. We help you to conceptualize, introduce and operate an effective patch management.
NextGen Firewall
We support you in the conception and implementation of security-technically effective firewall systems, in which the content of the data packets is analyzed in detail in order to detect and block malware, DoS attacks, cross-site scripting and SQL injections as early as possible. When designing the concept, we take into account all extended functionalities such as deep learning, intrusion prevention system, sandboxing, advanced threat protection, SSL inspection and multiple AV scans.
Our Solution
- Individual advice on existing ones
and potential security risks - Penetration Test – Analysis of your IT infrastructure with regard to acute security risks and security gaps
- Development of recommendations for action,
to maximize your IT Security - Implementation of security measures,
even while production is running - Training of your employees in safe handling
with data, user accounts and Co. - Definition of the necessary organizational
and technical measures - Awareness Measures – Investigating your employees’ reactions to attempted fraud
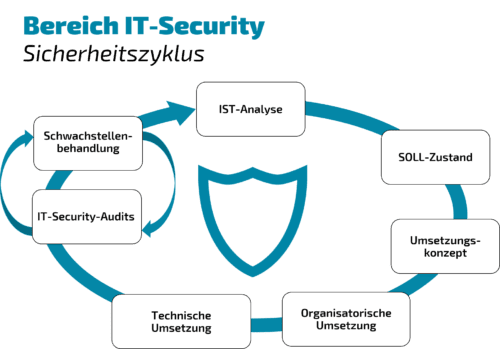
IT Security as an overall concept
Your profit
Experience:
You benefit from our routine in the area of IT Security at large companies
Efficiency:
Fast results thanks to CCVOSSEL-exclusive tools and diagnostic programs
Practicability:
You will receive implementable solutions that ensure safety in everyday work
Know-how:
Employee training ensures the transfer of knowledge from us to you
Productivity:
The security measures are also implemented during ongoing operations
Reference security
- Oliver Falkenthal is one of the authors in the “Guide to the state of the art in IT security” of the German IT Security Association (TeleTrusT).
- IT Security for over 800 servers, our approach on example CCAWARE –
Our free tool for time-saving, entertaining employee training

Sylwia Batashki
Team AssistantWe are always there for you personally.
We are located in the heart of Berlin and this is exactly where you end up when you call us. In this way we can react quickly and easily to your concerns, from which we then work out solutions together.
When placing the order, you will be provided with a permanent contact person from the department who you can reach directly. This ensures clarity and makes it easier for both sides to provide support during the project and subsequent support.

